Currently, if you create a Key Vault together with a Private Endpoint directly at the time of deployment, you won’t be able to access it via the internet, even if you enter your public IP address in the service’s firewall, afterwards…
The problem is, that the attribute „publicNetworkAccess“ is set to „Disabled“ when creating the Private Endpoint at deployment time. And it won’t be updated to „Enabled“ if you change the settings within the Firewall settings. Therefore, the public access (even only from a specific IP address) is forbidden.
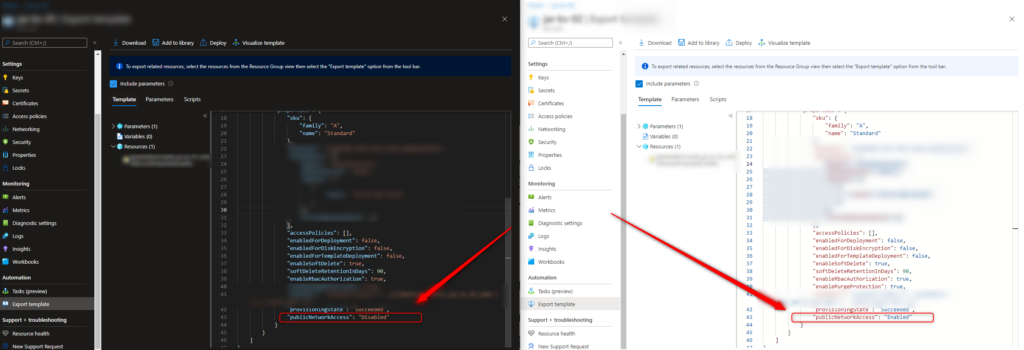
If you FIRST create a publicly available Key Vault and disallow the public access afterwards, together with adding a Private Endpoint, the setting is first set to „Enabled“ and remains „Enabled“ afterwards. So, you only run into this issue if you lock everything down first, and try to open up afterwards.
To enable this access (if desired), you need to use the CLI and update the respective Key Vault:
az keyvault update --public-network-access enabled --name YourKVName --resource-group YourRGNameOn the other hand, if you want to lock down the access, you should also make sure it’s locked tightly, by using the same code but just turn it around:
az keyvault update --public-network-access disabled --name YourKVName --resource-group YourRGNameRemember: You still need to make sure the Access Policies are configured properly, etc.
Enjoy.